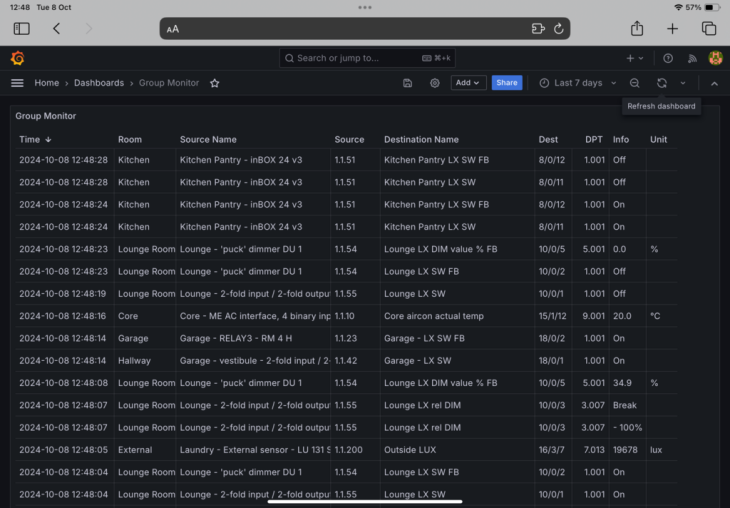
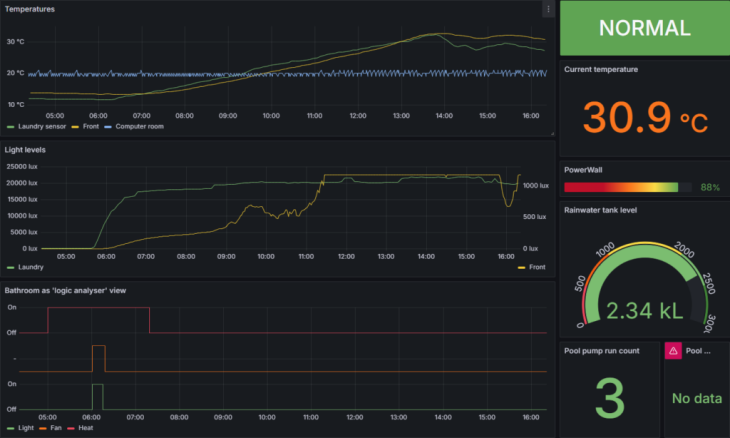
This July 1 2025 update to Skype for Business is somewhat momentous. In what looks to be ‘a giant leap for SfB-kind’, it takes a server running March 2025’s 7.0.2046.548 all the way to 7.0.2046.810.
|
This is no ordinary Cumulative Update!
To install this CU you need to “move” your servers using Topology Builder to the new “Skype for Business Subscription Edition”. You would have followed this process previously if you’ve performed an in-place upgrade from, say, SfB2015 -> 2019. |
Skype for Business Server Subscription Edition (SE)
Skype for Business Server Subscription Edition (SE) was released for general availability on July 1, 2025. The Skype for Business Server SE RTM build can be installed as a cumulative update (CU) to Skype for Business Server 2019, and it can be joined to your organizations. The version number of this update is 7.0.2046.810.
Skype for Business Server SE introduces changes to how SFB SE is serviced and licensed. This means there is no fixed end date for support, provided that configurations remain current. The product will be serviced continuously as an evergreen release, with no additional major, year-based versions planned for the future release.
For more information about the upgrade process, see Upgrading your organization from current versions to Skype for Business Server SE.