We had a new Widget arrive in the house recently, and it required a connection to the Wi-Fi network. It was duly connected to the untrusted ‘IoT’ network, where it’s denied Internet access by default. It WASN’T happy.
The supplier assured me it *didn’t* require Internet access, so I set about finding out what was going on, and Wireshark was going to figure into that equation.
A brief web search revealed that the Ubiquiti UniFi Access Points have “tcpdump” installed, and in conjunction with PowerShell and WinSCP I had my answers. Here’s how I did it.
How-To
For this process you’ll need to know the IP address and login credentials of your AP, and ideally the IP address that’s been allocated to the Widget. If you’re using VLANs, you’ll need the VLAN ID.
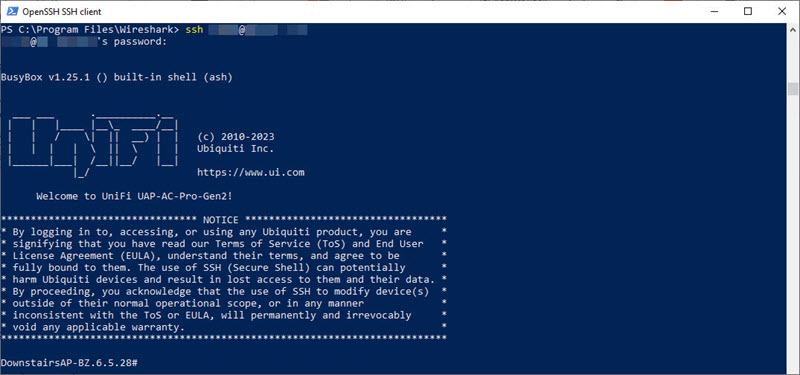
- Open a PowerShell window and login to your AP, using the format “ssh <username>@<ip address>:
ssh user@10.10.10.1
- You’re going to be saving a file locally, so let’s see where you are in the file system:
pwd

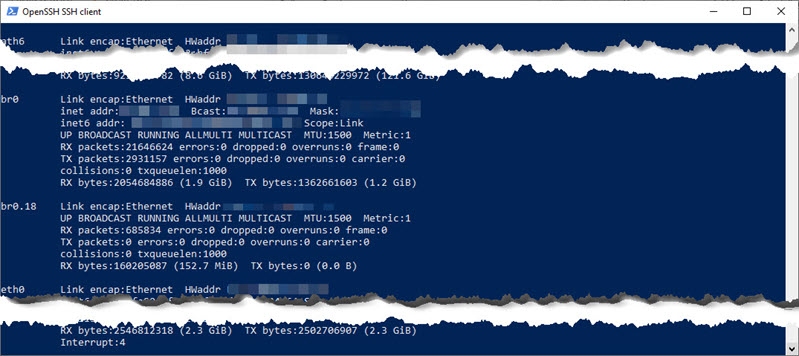
OK, so we’re in /etc/persistent. We’ll need to know that later. - Now do an ifconfig so we can determine which NIC to sniff.
ifconfig
- Scroll back until you get to “br0”. Its associated text should report the IP address of the Access Point. If you’re using VLANs, you’ll see them here as well, denoted as “br0.<VLAN_ID>”. In this example our IoT VLAN is 18:
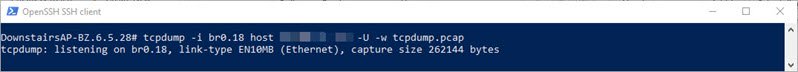
- OK, it’s showtime. This command will commence monitoring VLAN 18, filtering *out* everything except the host on 10.10.10.10 and saving the file to “tcpdump.pcap”:
tcpdump -i br0.18 host 10.10.10.10 -U -w tcpdump.pcap
Or just “br0” if you’re not VLANning:
tcpdump -i br0 host 10.10.10.10 -U -w tcpdump.pcap
Want to capture EVERYTHING? Omit the “host 10.10.10.10” bit:
tcpdump -i br0 -U -w tcpdump.pcap
- When you’re finished reproducing your issue, just Control-C to abort the tcpdump.
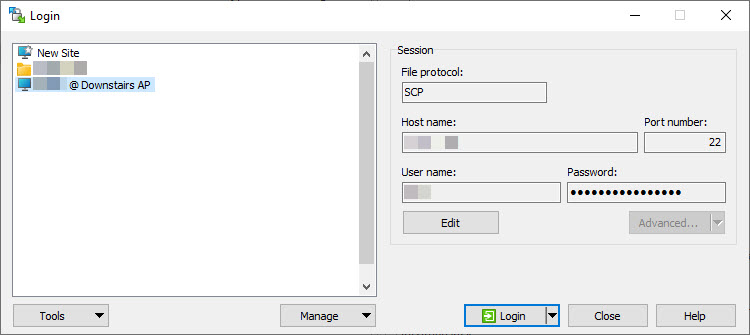
- Now you just need to transfer the file from the Access Point back to your PC. I used WinSCP for this:
- Now you can open the file in Wireshark and all the info you’re seeking will hopefully be revealed.
References
- How to run a remote packet capture with Wireshark and tcpdump
- Thank you Lawrence: Using Wireshark With UniFi Access Points for Real Time Packet Capture
Revision History
10th June 2023: This is the initial publication.
– G.