Microsoft has published a Critical security bulletin (MS13-054) detailing a “Vulnerability in GDI+ [That] Could Allow Remote Code Execution (2848295)”.
“This security update resolves a privately reported vulnerability in Microsoft Windows, Microsoft Office, Microsoft Lync, and Microsoft Visual Studio. The vulnerability could allow remote code execution if a user views shared content that embeds TrueType font files”.
The bulletin is HERE.
Products impacted
It seems quite a significant potential vulnerability (noting that it was ”privately reported”), with potential impact to all the operating systems released in the last decade, from XP to Windows 8, RT & Server 2012, as well as Office from 2003 to 2010.
In the UC space, it impacts the following products:
- Lync 2010 (4.0.7577.4392)
- Lync 2010 Attendee (4.0.7577.4392)
- Lync 2013 & Lync 2013 Basic (15.0.4517.1004)
I’ve also placed the download links on the respective Lync Resource Toolkit pages (at the very top of the right-hand menus).
A Silver Lining
It would seem that when a Hotfix like this is released, we also get the latest “working version” of the client update. Accordingly, some improvements to Lync 2013 have snuck into this release, although they’re not formally documented. Blogging power-house Matt Landis has collated several of the ‘found’ improvements HERE, which include:
- Meeting Q&A Feature (via Santiago Buitrago | English Translation)
- There is now a Lync Meeting Tab (via Santiago Buitrago)
- Instant Messaging Mute in Meetings! (via MasteringLync)
- Copy and Paste Pictures Into Lync! (via MasteringLync)
- Some security patch
Thanks to all for unearthing and posting these beauties!
Before & After
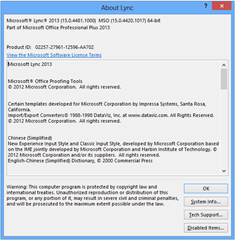
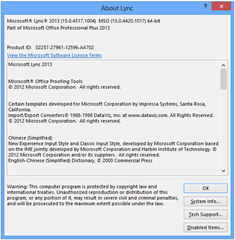
Here are the before and after shots from both the full version of the Lync 2013 client. I decided to exit the client before I applied the update, but alas, I still needed the reboot:
| Before (with May Hotfix) | After |
| Lync 15.0.4481.1000 MSO 15.0.4420.1017 | Lync 15.0.4517.1004 MSO 15.0.4420.1017 |
 |
 |
G.