I recently hit a brick wall while trying to update a certificate template in my stand-alone Server 2016 Certificate Authority.
My goal was to add the “Client Authentication” policy to the the Web Server template, but whilst I could create the new template without any problems, Windows wouldn’t let me add it to the list of “certificates to issue”.
Copying Templates
The process to copy a certificate template is fairly well documented. The short version is:
- Launch the Certificate Authority MMC:
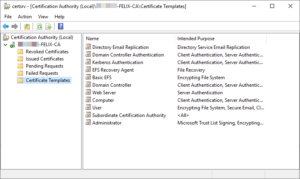
- Right-click Certificate Templates and select Manage, which opens the “Certificate Templates Console”.
- Right-click on the certificate you want to copy and select Duplicate Template.
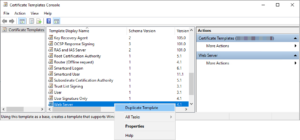
- Make the required changes to this template, including of course giving it a new name on the General tab:
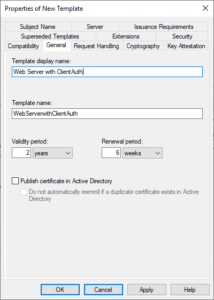
- OK to save.
- Close the Certificate Templates Console.
- Revert to the Certificate Authority MMC.
- Right-click Certificate Templates and select New / Certificate Template to Issue:
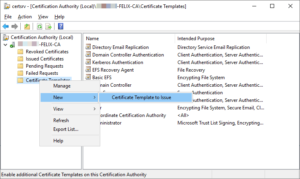
- On the Enable Certificate Templates dialog, click the new template and… Hang on: it’s not there!
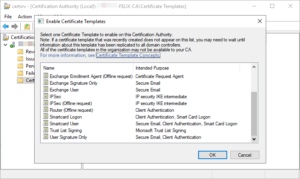
Much Googling revealed a range of suggested fixes. Most of those centred on permissions on the Security tab, with a few suggesting changes to the Compatibility and Subject Name tabs, but none of them worked.
It took me ages to stumble on it (and months passed in between attempts at resolving this) but in the end it was something as simple as using certutil to do what the GUI wouldn’t:
PS C:\> certutil -setcatemplates +WebServerwithClientAuth 0: WebServerwithClientAuth: Adding CertUtil: -SetCATemplates command completed successfully. PS C:\>
BAM!
(Note in the above you need to use the template’s “Template Name” (see the image in Step 4).
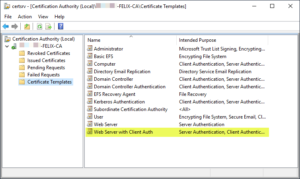
It’s now visible in the Certificate Authority MMC:
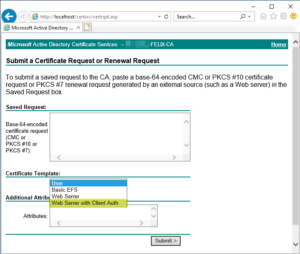
… and also the web enrolment page:
Credit
If found the fix in Vadims Podāns’ Certificate Autoenrollment in Windows Server 2016 (part 3).
Revision History
12th September 2020. This is the initial publication.
– G.




Having a very similar problem. Being that the symptoms are identical but none of your proposed solutions are working. There used to be a seperate CA on the network, but that server has been long decommissioned. I can’t help but think that there isa reference to the old server somewhere that is preventing the Certificate Template from being recognized.
I verified that the Server is an Enterprise Root via regedit:
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration\\CAType = 0
Hi
You saved my day! Your solution worked perfectly. In my case I have migrated a CA to a new server and I could not add a template.
Does anybody know why this is sometimes happening?
Thanks again
Axel
Hey man,
That’s exactly what I was searching for, you’ve saved my day.
I’ve migrated CA to a new server and had exactly that issue that I couldn’t issue my templates to make them available. Thanks for your tip with certutil, it’s a mess that it cannot be done in the GUI, but with certutil. (facepalm)
I had the same problem, after migration to Win2022 couldn’t add any template using GUI. Thanks to this article.
Dear Greig Sheridan,
Thank you very much, this has saved me after a long period of researching on how to show duplicated certificate template in the CA. Mine was on Windows Server 2019 so this solution worked.
Thank you so much! I just migrated to a new CA with a different computer name and in the Manage portion of Certificate Templates in the certsrv program I could see the custom templates but when I clicked “new certificate template to issue” they didn’t come up. The Powershell certutil command added them in for me!
Wow, I’ve been scratching my head on that problem for a week and finally the problem comes from the GUI, amazing, thanks for this very usefull information. Certutil to the rescue