The Sonus/Ribbon Enterprise family of SBCs has a great feature where it can use your Active Directory as both a means to authenticate logins, and also to dynamically make changes to your call routing.
It does this by using a service account to authenticate to AD and query the relevant attributes or group membership, depending on which of the above features is involved.
Whilst the password to this account is saved in the backup files and encrypted, I recently found that if you possess a REST login for the SBC you can use that to recover the password.
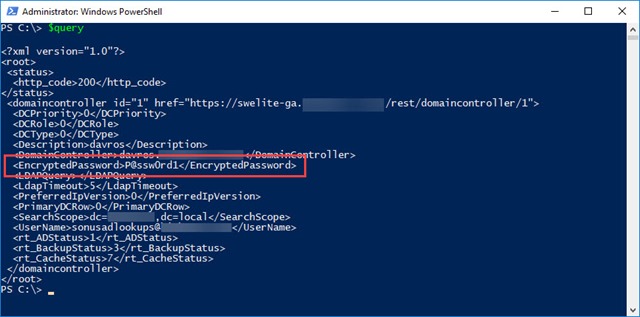
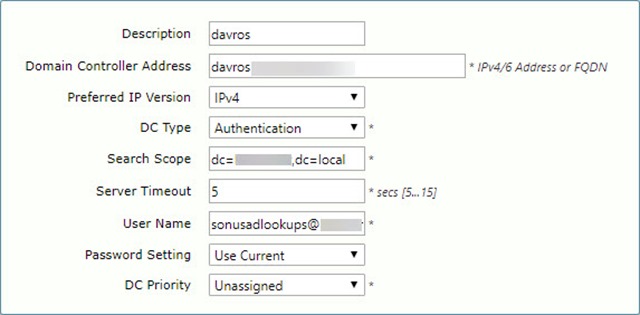
Here’s the relevant entry in the Domain Controllers table from my SBC:
And here’s the P$ to recover the password:
$SbcFqdn = "mySBC.contoso.com" $RestLogin = "myRestLogin" $RestPassword = "myRestPassword" $BodyValue = "Username=$RestLogin&Password=$RestPassword" $url = "https://$SbcFqdn/rest/login" $Query = Invoke-RestMethod -Uri $url -Method Post -Body $BodyValue -SessionVariable SessionVar $url = "https://$SbcFQDN/rest/domaincontroller/1" $Query = Invoke-RestMethod -Uri $url -Method GET -WebSession $SessionVar $Query
Obviously for the above you need to have a REST login for this SBC. If you don’t already have one of those, that can be created under Security / Users / Local User Management.
The only other point to mention in the above is the “1” I’ve highlighted at the end of the domain controller query. That needs to be the number of the “Primary Key” of the DC you want to query. That’s the value at the far right of the Domain Controllers table.
Tada!
Security Risk?
Are you a glass half-full or a glass half-empty person?
Because this password is only recoverable by you through an encrypted (https) REST session, for which you need a valid REST login to the SBC, Ribbon deems this not to be a security risk.
It does however demonstrate the need to diligently manage the rights of service accounts you use for third party products like the SBC.
Resources
Read some more about REST and the DomainController query here:
Revision History
25th July 2018. This is the initial release.
– G.




I think you nailed it on the head there with the line “diligently manage the rights of service accounts”
Whilst I don’t see an issue with it being recoverable myself some orgs have some pretty serious requirements around this.
If Sonus are going to tell us we cant have access to the shell on the box any more for “Security” then we should have the option to harden this too.
This should totally be an option “Allow Password Recovery via REST”.
(probably during initial setup or when you enter the creds)
Imagine if you will an appliance setup initially by internal staff not really understanding the technology then handing the management over to a 3rd party integrator.
I get given a password to the Sonus appliance and create myself a REST account, only to find that at some point “for testing” someone used domain admin creds for LDAP and forgot to change it.. I now have the ability to potentially recover a domain admin account.
We all know that best practice says this shouldn’t happen, but unfortunately not everyone follows best practice. And just like we have to protect users from themselves. We need to protect businesses from cowboy admins.