Updated Apr30th: 5.0.2 Rev D (aka 5.0.2.2756) is out, with a Heartbleed fix
In case you missed it recently, Polycom’s released v5.0.2 of its UCS firmware (which is what powers the VVX family of phones). The focus in this release is on improving its stability and the readme certainly packs a mammoth list of fixes to known issues, including problems with complex regex in dial plan normalisation rules plus transfer and pickup problems, to name but a few.
The BToE connector utility for your PC hasn’t been updated and remains at v2.0.1.
Download
You can find the whole shebang here, but you wouldn’t be the first person to be blinded by the collation of links. Here are the key ones:
Firmware / Software
- UC Software 5.0.2 Rev D for VVX Business media Phones and SoundStructure [Split]
- CAB file for UC Software 5.0.2 Rev D for upgrades from Lync Server
- Better Together over Ethernet Connector (BToE) Application 2.1.0
Documentation
Polycom updated the 5.0.2 Release Notes PDF after the initial release. You can tell if you have the latest version if you have a Table 4 that’s not “TBC”.
- UC Software 5.0.2 Release notes for VVX Business media Phones and SoundStructure
- UC Software 5.0.2 Rev D Release notes for VVX Business media Phones and SoundStructure
- UC Software 5.0.1 Administrators’ Guide
Installation
If you’re already running the VVXs with a version of 5.0.x using Lync for the firmware provisioning, simply bung the CAB file version of the firmware on the Front-End server, let Pat’s script load it for you, and just approve it from the Lync Control Panel.
If you’re not there already, I’ve written a little more about the process here, and my recommended config file is here.
Heartbleed
The Heartbleed OPENSSL exploit exploded publicly at about the same time as 5.0.2 was released and Polycom’s “SECURITY BULLETIN CVE-2014-0160 Version 1.6” (current as at this writing – 23rd April) leaves me with more questions than answers about the UCS firmware for the VVX. UCS firmware up to 5.0.1.7396 is shown as vulnerable, and the fix is “5.0.2” due April 24th – later this week. So is the current two-week old release (formally “5.0.2.2185”) in the clear or not?
Perhaps it doesn’t really matter anyway. The mitigation for any exposed phones is simple: just set httpd.enabled=0, and as Polycom says “This disables web access of all kinds, and blocks known heartbeat vectors into the system”.
Oh, and 5.1 (the new feature update release) is expected to GA ~May 6th anyway. Watch this space.
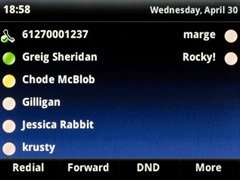
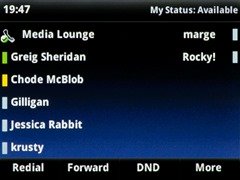
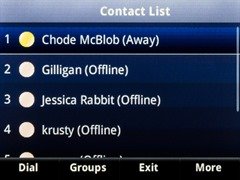
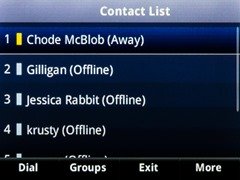
Before & After
The look and feel of these is certainly improving. In the top row of photos you can see (at the top left) we now see the logged-in user’s name instead of their phone number, and the “offline” colour is now grey, consistent with the Lync client and no longer the indistinct faded apricot of before.
 |
 |
 |
 |
Revision History:
I’ve made several changes to this post since it was first published on April 23rd. The links were updated on the 30th with the new Heartbleed-fix version, and I also added the before and after shots. I’ve also taken the liberty of correcting a small error from the Polycom Security Bulletin: it says you use “http.enabled” to disable the web-browser, but it’s correctly “httpd.enabled”.
– G.



